Identity Proofing vs. Identity Verification: Key Differences Explained

Businesses need more than just a customer’s name and email to ensure security. Fraudsters are increasingly sophisticated, and compliance regulations demand strict identity checks. That’s where identity proofing and identity verification come into play. While the two terms are often used interchangeably, they serve distinct roles in building trust and preventing fraud. This article breaks down the differences, explains how they work together, and explores why both are essential for secure and seamless digital onboarding.
What is Identity Proofing?
The Identity proofing process includes collecting and validating personal information to prove that an individual is real and truly who they claim to be. It acts as the foundation of trust in digital interactions, ensuring that businesses are not dealing with fabricated or stolen identities. Without this first layer of security, even the most advanced identity verification measures can fall short.
How Identity Proofing Works
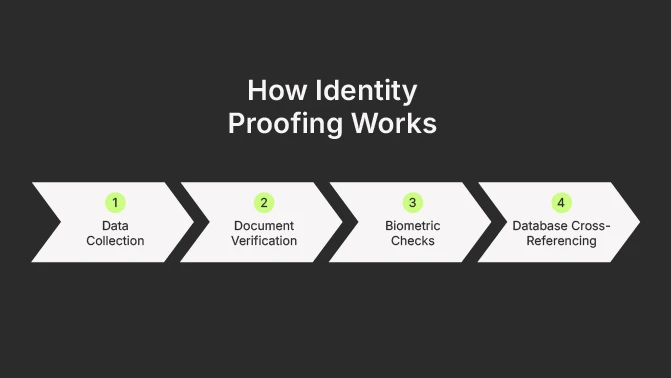
1. Data Collection
The process begins with gathering basic information such as a person’s full name, date of birth, address, and government-issued ID numbers. This initial data creates the “identity footprint” that will later be checked against reliable sources. While it may sound straightforward, accuracy at this stage is critical and false or incomplete details can compromise the entire process.
2. Document Verification
Once the personal details are provided, users are typically asked to submit official documents like a passport, driver’s license, or national ID card for document verification. These documents are then scanned and analyzed for authenticity. Advanced systems can detect subtle signs of forgery, such as mismatched fonts, tampered photos, or invalid expiration dates, making it difficult for fraudsters to slip through with counterfeit IDs.
3. Biometric Checks
To ensure that the individual presenting the documents is the rightful owner, biometric checks are introduced. Facial recognition technology compares a live selfie or video with the photo on the submitted ID. Liveness detection adds another layer by verifying that the person is physically present (and not a deepfake or static image). In some industries, additional biometrics like fingerprints or voice recognition may also be used.
4. Database Cross-Referencing
The final step involves comparing the collected information against trusted databases, such as government registries, credit bureaus, watchlists, or sanctions databases. This step ensures that the identity is not only valid but also not associated with suspicious activities like fraud, money laundering, or terrorist financing.
The Outcome of Proofing
By combining these steps, businesses can establish that the identity in question is both real and legitimate. Successful proofing helps organizations build a strong defense against impersonation, synthetic identities, and other forms of fraud. It also provides the essential baseline that allows for ongoing verification throughout the customer’s lifecycle.
Why is Identity Proofing Important?
Identity proofing is a safeguard that underpins secure digital relationships. By ensuring that individuals are who they claim to be, organizations can protect themselves, their customers, and the wider financial ecosystem from serious risks.
Compliance with Global Regulations
Regulatory frameworks such as Know Your Customer (KYC) and Anti-Money Laundering (AML) require businesses to verify customer identities before providing services. For financial institutions, telecoms, healthcare providers, and even digital marketplaces, failing to comply can result in hefty fines, sanctions, or the loss of operating licenses. Identity proofing helps businesses meet these obligations while maintaining smooth customer onboarding.
Shielding Against Onboarding Fraud
One of the fastest-growing threats is synthetic identity fraud, where fraudsters combine real and fake information to create entirely new identities. Without robust proofing, these fraudulent profiles can slip through onboarding processes, opening accounts, accessing services, and committing crimes under a false identity. Effective proofing prevents these risks by verifying documents, checking biometrics, and cross-referencing databases before granting access.
Building Customer Trust
Customers want to know that the organizations they engage with take their security seriously. A strong proofing process reassures users that their personal data is protected and that the platform they’re joining is safe from bad actors. This trust translates into loyalty as it makes customers feel secure and they are more likely to complete the onboarding journey and continue using the service.
Supporting High-Security Industries
Some industries simply cannot afford weak identity controls:
- Banks and fintechs rely on proofing to stop money laundering, account takeover, and fraudulent transactions.
- Healthcare providers use it to ensure that sensitive patient records are accessed only by the right people.
- E-commerce platforms apply proofing to prevent fake accounts, fraudulent purchases, and chargeback schemes.
In each of these sectors, proofing is the first barrier against fraud and abuse.
The Cost of Weak Proofing
Without strong identity proofing, businesses open themselves up to severe consequences:
- Financial losses from fraud and scams.
- Regulatory penalties for non-compliance.
- Reputational damage that erodes customer trust and drives users to competitors.
In short, identity proofing is not just about compliance—it’s about protecting revenue, maintaining credibility, and creating a safe environment for legitimate customers.
What is Identity Verification?
Identity verification is the process of confirming that the identity information provided is authentic and that it genuinely belongs to the person presenting it. While identity proofing focuses on collecting and building an identity profile, verification is about validating its accuracy and legitimacy. Together, they form the backbone of secure onboarding and ongoing digital trust.
Unlike proofing, which is often a one-time process at the beginning of a relationship, verification can be applied continuously or repeatedly—for example, when logging in, making transactions, or accessing sensitive data.
Types of Identity Verification
1. Document-Based Verification
This method involves analyzing government-issued IDs such as passports, driver’s licenses, or residence permits. Advanced technology checks security features like holograms, fonts, barcodes, and expiration dates to detect forgeries. For example, banks often require customers to upload a photo of their ID alongside a selfie, ensuring the document matches the person using it.
2. Biometric Verification
Biometric methods compare unique physical or behavioral characteristics against stored identity data. Common approaches include facial recognition, fingerprint scanning, iris recognition, and even voice authentication. Biometric data verification is increasingly popular because these traits are hard to fake or steal. Liveness detection technology is also used to prevent fraud attempts with deepfakes or static photos.
3. Database Verification
In this method, the individual’s details—such as name, date of birth, or national ID number—are cross-checked against reliable databases. These can include government registries, credit bureaus, sanctions lists, or watchlists. Database checks are particularly useful in financial services, where compliance with AML and KYC laws requires institutions to screen customers against international risk databases.
4. Knowledge-Based Verification (KBA)
This approach asks users to answer personal questions, such as “What was the name of your first school?” or “Which address have you previously lived at?” While once common, KBA has lost popularity because much of this information is now accessible on social media or the dark web, making it less secure.
5. Two-Factor Verification (2FA)
Two-factor authentication adds an extra layer of protection by requiring users to verify their identity through a second channel. This could be a one-time password (OTP) sent by SMS or app, a push notification, or a hardware security key. While not foolproof, 2FA significantly reduces the risk of account takeover by ensuring that a compromised password alone cannot grant access.
Why Verification Matters
Verification is critical because it ensures that the identity established during proofing is real, accurate, and continuously protected throughout a customer’s journey. It reduces the likelihood of fraud, prevents unauthorized access, and helps organizations maintain compliance with strict security and privacy standards.
In practice, modern businesses rarely rely on just one method. Instead, they adopt a multi-layered verification strategy that blends document analysis, biometrics, and database checks with ongoing 2FA. This creates a strong defense system that balances both security and user convenience.
Identity Proofing vs Identity Verification: Main Differences
| Aspect | Identity Proofing | Identity Verification |
| Purpose | Establish that an identity exists | Confirm authenticity of identity |
| Process | Collect and build an identity profile | Validate collected data is accurate |
| Timing | Initial stage of onboarding | Ongoing, recurring checks |
| Example | Uploading an ID document | Matching a selfie to the photo on the ID |
Identity Proofing and Verification in Practice
Proofing and verification are not rivals—they are partners in secure digital onboarding. Businesses typically use proofing at the start to build a customer identity profile, then apply verification methods repeatedly to maintain trust throughout the relationship.
This dual approach is also a regulatory requirement. Standards like KYC, AML, GDPR, and NIST highlight the need for robust identity management. Many modern platforms now combine proofing and verification tools into a single, seamless solution, reducing friction while maintaining compliance.
Benefits of Strong Identity Proofing and Verification
Implementing robust identity proofing and verification processes offers significant advantages for businesses and their customers. These benefits go beyond compliance—they directly influence security, customer experience, and operational success.
Fraud Prevention
The most immediate benefit is protection against fraud. By combining proofing and verification, businesses can stop impersonation, account takeovers, and synthetic identities before they cause damage. Document checks, biometric verification, and database cross-referencing create multiple layers of defense, making it extremely difficult for bad actors to bypass security. This not only safeguards financial assets but also prevents reputational harm from fraud incidents.
Regulatory Compliance
Compliance with strict frameworks such as KYC, AML, and even GDPR (General Data Protection Regulation) is non-negotiable for many industries. Strong proofing and verification processes ensure that customer identities are validated in line with these requirements. Beyond avoiding fines and penalties, compliance also signals professionalism and reliability to regulators, partners, and customers.
Customer Trust and Confidence
Onboarding is often a customer’s first real interaction with a business. A secure and transparent process builds confidence that the company takes data protection seriously. Customers who feel safe are more likely to complete registration, engage with services, and remain loyal in the long term. In industries like banking, fintech, and healthcare, trust is a competitive advantage that sets businesses apart.
Operational Efficiency
Manual identity checks are resource-intensive and prone to human error. Automated proofing and verification solutions reduce the workload for compliance teams by streamlining document validation, biometrics, and database checks. This not only saves time and money but also speeds up onboarding, allowing legitimate customers to start using services faster. In a competitive market, reducing friction in the onboarding process can mean the difference between winning or losing a customer.
Long-Term Security and Scalability
Beyond initial onboarding, strong proofing and verification systems support ongoing identity checks throughout the customer lifecycle. This is especially important for high-risk activities like large financial transactions, account recovery, or accessing sensitive data. Businesses benefit from scalable systems that can adapt to growing customer bases while maintaining security at every stage.
Future of Identity Proofing and Verification
The future of identity proofing and verification lies in smarter, more seamless technology that balances security with user experience. Artificial intelligence is already being used to detect deepfakes and forged documents, while biometrics such as facial recognition and voice authentication are becoming standard for everyday access and transactions. At the same time, reusable digital identities are emerging, allowing customers to carry secure credentials across multiple platforms without starting from scratch each time. These innovations are shaping a shift toward frictionless onboarding, where businesses can meet strict compliance demands while delivering faster, safer, and more user-friendly experiences.








