Authentication Tools
Make your returning user’s journey more accessible without sacrificing secure authentication. Make the most of the data you already have and double-check the user during multi-factor authentication with various tools without making the process tedious.
Authentication Methods and Other Tools
Security Beyond Authentication
Authenticate Your Client’s Age
Use biometric authentication to detect the user's age without any document or needing to rely on e-signature authentication. Our solutions adapt to your needs to create compliant and convenient authentication methods for your users.
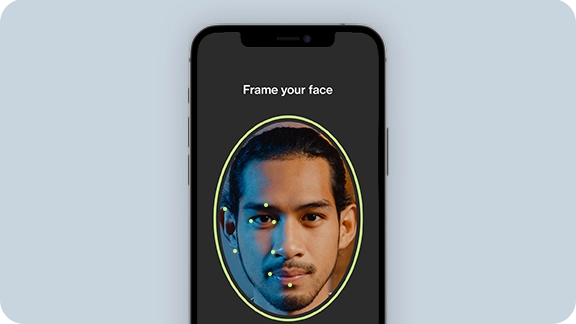
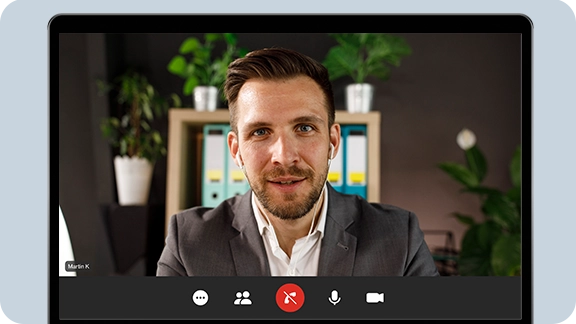
Identity and Access Management for Online Meetings
Introduce a high-grade authentication mechanism before allowing users into your video meetings. After performing a short identity verification check, the user is allowed into the meeting, making it a genuinely confidential means of remote communication.
Why Clients Trust Ondato
FAQ
Currently, with returning user verification the false acceptance rate is 1 in 12,800,000 while the false rejection rate is less than 1%.
The best authentication method depends on your company's needs. However, one authentication method that stands out above all else is multi-factor authentication (MFA), also known as two-factor authentication (2FA). Still, when deciding the best method for your business, it's important to look at risk-based authentication: how much risk does authorization and authentication for your product bring and what are the needs of your customers.
Authentication can be classified into three groups: something the user knows: a password or PIN; something the user has: an access or bank card; something the user is: biometrics, such as fingerprints or face recognition.
Authentication management tools are systems set up to provide secure access to your data. Biometric authentication, device management, e-signatures - they are all ways to prove access to information should be granted.